
At Iglum Technologies, we believe in building strong, long-lasting relationships with our clients, and we are dedicated to helping them achieve their goals and grow their businesses.
Core Features
The full service we are offering is specifically
designed to
meet your business needs.
Protecting Your Business from the Unknown
Cloud Security Monitoring and Incident Response.

Use Case:
A rapidly growing fintech company that operates exclusively in the cloud is increasingly concerned about the security of their sensitive financial data. The company has already invested heavily in security measures but they want to ensure that their cloud infrastructure is continuously monitored and that they have a solid plan in place in the event of a security incident.
Problem:
The fintech company is concerned that they are not able to effectively monitor their cloud infrastructure for security threats. They also lack a comprehensive plan to respond to security incidents, which could result in serious consequences for their business and their customers.
Solution:
By implementing a cloud security monitoring and incident response plan, the fintech company can proactively monitor their cloud infrastructure for potential threats, identify and respond to incidents in a timely manner, and minimize the impact of a security breach.
This includes tools such as cloud access security brokers, network monitoring, endpoint detection and response, and incident response planning and testing. By investing in cloud security monitoring and incident response, the fintech company can protect their business and their customers from potential security threats in the cloud.
Ensuring Compliance for a Healthcare Startup

Use Case
A healthcare startup that processes sensitive patient data needs to comply with HIPAA regulations to protect patient privacy. The startup is struggling to keep up with the constantly evolving regulatory landscape and the burden of maintaining compliance is hindering their ability to innovate and grow.
Problem
The healthcare startup is finding it difficult to manage and stay up-to-date with the complex and constantly changing regulations related to HIPAA compliance. The manual process of tracking compliance is taking up valuable time and resources, making it difficult for the startup to focus on developing new features and scaling their operations.
Solution:
By implementing a compliance management solution like AWS's HIPAA Compliance Program, the healthcare startup can streamline their compliance efforts and focus on their core business.
The compliance management solution provides a framework for maintaining HIPAA compliance and automates many of the manual processes involved in compliance tracking, reducing the burden on the startup's resources.
With a dedicated compliance team and automated tools in place, the healthcare startup can ensure that they are meeting HIPAA requirements while still being able to innovate and grow.
"Protecting Your Digital Assets:
The Importance of Threat and Vulnerability Management"

Use Case:
A medium-sized financial services company is expanding their digital presence with a new mobile banking app. They are concerned about the potential security risks and vulnerabilities that could be introduced with the new app and want to ensure they are properly managing threats and vulnerabilities to protect their customers' sensitive financial information.
Problem:
With the new mobile banking app, the company is potentially exposing themselves to new security risks and vulnerabilities that they need to proactively manage. Without proper management of threats and vulnerabilities, the company could face reputational damage, loss of customer trust, and financial repercussions.
Solution:
By implementing a threat and vulnerability management solution like Qualys, the financial services company can proactively identify, track, and remediate security threats and vulnerabilities across their entire IT infrastructure.
This solution can help them keep their mobile app and other digital assets secure from cyber threats such as malware, ransomware, and hacking attempts.
With continuous monitoring and analysis of their IT infrastructure, they can ensure they are always up-to-date with the latest security patches and measures, while also minimizing their exposure to risk.
"Protecting Your Business in the Cloud:
Cloud Security Architecture and Design"
Use Case
A mid-sized business is migrating their data and applications to the cloud to improve scalability, flexibility, and cost-effectiveness. However, they are concerned about the security risks of hosting sensitive information on the cloud and want to ensure their data is protected against potential cyber attacks.
Problem
As more businesses move their operations to the cloud, there is a growing need for strong security measures to protect sensitive data and prevent security breaches. However, developing a robust security architecture that can effectively protect against cyber threats can be challenging, particularly for businesses with limited security expertise.
Solution:
Cloud Security Architecture and Design is a comprehensive approach to protecting data and applications hosted on the cloud. By leveraging industry best practices and cutting-edge technologies, businesses can design and implement a secure cloud environment that can protect against a wide range of threats, including malware, phishing, and data breaches.
Cloud Security Architecture and Design involves a multi-layered approach that includes network security, access control, identity management, and encryption, among others. With a strong cloud security architecture in place, businesses can enjoy the many benefits of cloud computing while also ensuring their data is secure and protected from cyber threats.
Securing Your Sensitive Data with Comprehensive IAM Solutions

Use Case:
A large financial institution with a diverse employee base needs to securely manage access to its sensitive data across various departments, systems, and applications. They want to ensure that employees have the right level of access to perform their job functions, while also protecting sensitive data from unauthorized access.
Problem:
The financial institution is struggling with managing employee access to different systems and applications. They have multiple access management solutions in place, but these systems are not integrated, causing inconsistencies and gaps in access control. This poses a significant security risk to sensitive data and could lead to compliance issues.
Solution:
By implementing a comprehensive Identity and Access Management (IAM) solution, the financial institution can ensure that only authorized users have access to sensitive data.
IAM provides a centralized system for managing employee access across all systems and applications, which makes it easier to monitor and enforce access policies.
With IAM in place, the financial institution can also ensure compliance with regulatory requirements and reduce the risk of security breaches.
How It Works
Find out everything you need to know
about
creating a business process model.
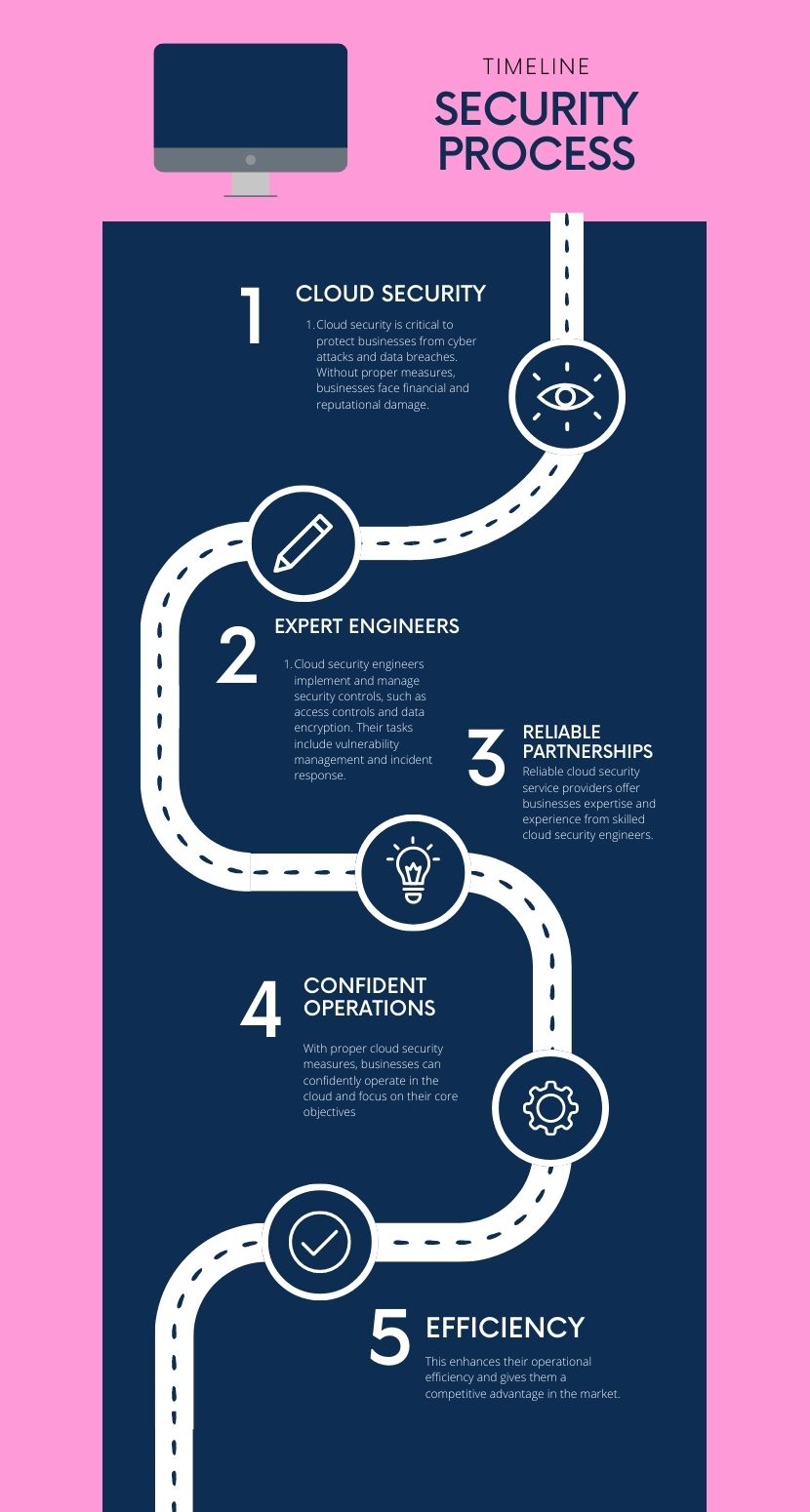
Cloud Security
Cloud security is critical for businesses that operate in the cloud, as it ensures the confidentiality, integrity, and availability of their data and applications. Without adequate security measures in place, businesses are vulnerable to cyber attacks, data breaches, and other security threats that can result in significant financial and reputational damage.
Expert Engineers
To ensure robust cloud security, businesses require the expertise of cloud security engineers who can implement and manage security controls across their cloud infrastructure. These engineers are responsible for implementing access controls, network security, data encryption, vulnerability management, and incident response, among other tasks.
Reliable Partnerships
By partnering with a reliable cloud security service provider, businesses can benefit from the expertise and experience of skilled cloud security engineers. Such providers can help businesses identify and assess their security risks, implement security controls, monitor and detect security threats, and respond to security incidents in a timely and effective manner.
Confident Operations
With the right cloud security measures in place, businesses can operate in the cloud with confidence, knowing that their data and applications are secure and protected from potential threats. This allows them to focus on their core business objectives, improve their operational efficiency, and gain a competitive advantage in the market.
Technologies we use









